P.I. Services
Private Investigations
Missing Persons
Background Reports
Surveillance Investigations
Unclaimed Assets
- Private Investigations
- Domestic Family Investigation
- Unclaimed Funds Investigation
- Asset Recovery
- Cell Phone Spyware Removal
- Data Extractions
- Litigation Investigation
What is a Private Investigator?
A private investigator is someone who is trained in the art of investigation and, in most states, is licensed to conduct investigations on someone else’s behalf for compensation. Private investigators gather information on behalf of another individual, business or law firm and most often has a signed retainer agreement, contract or other letter of authority from the client authorizing his or her inquiry.
What is the difference between a Private Investigator and Law Enforcement?
One way to answer the question “What is a private investigator?” is to state what a private investigator is not. A private investigator is not a law enforcement officer. A law enforcement officer is hired by a government agency to investigate criminal matters as opposed to civil matters. Police investigations are conducted by sworn law enforcement officers and done within the constraints of Constitutional laws. The investigation is conducted to determine if a crime has been committed, to determine who committed the crime, and to gather enough evidence to present to a prosecutor for a trial.
A private investigator is an average citizen who is hired by an individual to investigate matters. Private investigators are not restricted to Criminal Investigation in Miami like police officers; as a private investigator, you will commonly be investigating civil matters as well. These matters include but are not limited to infidelity investigations, background investigations, asset location investigations, or fraudulent insurance claims.
Private investigators may uncover criminal violations, but work at the behest of their clients not a law enforcement agency or body.
As investigators we are in the information business; in relentless pursuit of the truth. Clients of course may not always want to hear the truth, but as a private investigator it is your essential job function to collect the facts, not withholding any of those facts (good or bad), use sound reasoning and judgment, and develop a factual account or conclusion from the information you have collected. The end result of your investigation should always explain the fundamentals: what happened, who was involved, when and where it occurred, and most importantly, why it happened.
As an investigator, you will be required to “think outside of the box”, make quick decisions, be creative and deal with a very wide variety of people in the process.
A private investigator must be detailed; someone who is an excellent note-taker, a researcher, a great communicator, and someone who takes great care to remain within the law. Keep in mind that many investigators spend time away from their offices, maintain irregular hours, and conduct assignments that can sometimes be arduous and mundane. In addition, some of your work may be confrontational, stressful, and even dangerous.
Ultimately, regardless of the complexity or nature of the investigation, private investigators essentially perform only a few basic functions in developing the evidence upon which our final report to the client rests (though the varying level of difficulty of each is what makes the job interesting):
- We talk to people. (Interviewing and Taking Statements)
- We find people. (Skip Tracing)
- We watch people. (Surveillance)
- We ask about people. (Background Investigations)
These are the four cornerstones of the business of private investigation in its purest definition and the rest of this manual has been developed with these concepts in mind.
A domestic disturbance is when an argument, usually between spouses, significant others, or family, becomes more than shouting at one another, and verbal abuse or psychological abuse occurs. If physical contact was made, you may be charged with domestic violence.
“Domestic investigation” is a general term describing investigations that revolve around individuals and their legal problems. Some of these problems could include fraud, theft, or abuse that occur in a person’s own home.
What types of domestic investigation are there?
Depending on your specific case, there are different types of investigation that your domestic investigator could use:
Domestic surveillance: When you leave your home, covert surveillance, like nanny cams or audio devices, can ensure your space and the people in it are safe while you’re away. The resulting photographs and video can also be used in court if a crime is committed on your property.
Background checks: When allowing someone into your home, a background check can confirm whether or not a person is trustworthy. These checks look into employment history, criminal records, education, references, civil records, and more.
Undercover or covert operations: Whether your spouse is cheating or someone is using illegal substances in your home, a domestic investigator is experienced in gathering evidence and documenting actions without being seen. They are also aware of the legal implications of conducting such an investigation.
Computer forensics: Often the evidence you need to prove misconduct in your home is on a computer or cell phone. An investigator can conduct a computer forensics investigation and collect emails, files, texts, and even deleted information that is relevant to the investigation.
Public record and information research: If you are being blackmailed, stalked, or need to file a restraining order, an investigator is capable of conducting a public record search and finding documents with pertinent information, like family history, criminal pasts, or current places of residence. This is similar to a background check but is more extensive and involves more resources.
People Locate: If you need to find someone for any reason, whether they are not providing child support or you need a process server, an investigator can conduct a skip trace and potentially find them for you.
Do I need a domestic investigation?
Domestic investigations are about protecting your home. If you are concerned about the safety of your possessions or loved ones for any reason, whether it’s an abusive family member or threat of an intruder, a domestic investigation will retain evidence of wrongdoing and prevent any future crime.
Some situations that call for a domestic investigation are:
- Cheating spouse
- Divorce and spousal deceit
- Bigamy
- Threats, blackmail, and extortion
- Restraining orders
- Stalkers
- Spouse or child abuse
- Missing person
Why hire a private investigator for a domestic investigation?
In the case of a domestic issue, it’s best to have an investigator conducting the investigation. Here’s why:
- An investigator will obtain all evidence legally so that it can later be used in court proceedings.
- When sensitive information is involved, investigators have access to resources that aren’t available to the public.
- Private investigators have been trained and have a wealth of investigative experience.
- Investigations will vary greatly depending on the case. An investigator will be familiar with a variety of methods and will know which to use in a given situation.
- An investigator will handle the information they discover in a professional and confidential manner.
For most states, the dormancy period is five years. When property is officially designated by the state as abandoned or unclaimed, it undergoes a process known as escheatment, where the state assumes ownership of that property until the rightful owner files a claim.
Unclaimed property needs its rightful owner. In Florida alone, more than $313 million of unclaimed property has been returned to those who live in the state. This is due to over 513,000 individual claims. That is a lot of property that would’ve otherwise been left unclaimed. You may have something in your name that you have forgotten about or need to claim but are unsure how to do it. That is where a private investigator comes into play.
What is Unclaimed Property?
From a legal perspective, this is a category of common law that deals with your personal property. This property has left the possession of the rightful owner but has never entered the possession of another. To put it simply, it is money or property that you have forgotten about.
Unclaimed Property Forms
- Unclaimed pay from a former employer
- Insurance payouts from policies of deceased relatives that were left unclaimed
- Security deposits from a house or apartment you rented
- The inheritance you never claimed
- A tax refund you never cashed
- Contents in a bank safety deposit box that was never picked up
- You have money in a dormant checking, savings, or money market account
- Brokerage accounts with bonds and stocks that you never closed
Let’s face it, you or your family deserves their unclaimed property. Unrecovered property or money needs its rightful owner. Here are some facts over unclaimed property:
- It is estimated that 1 out of 10 people have unclaimed property
- There is nearly $58 billion in unclaimed property and money
- Their rightful owners ever recover only 5% of these unclaimed properties
How Can a Private Investigator Help?
A private investigator can conduct research into financial matters and track down money that may belong to you. They are qualified in the latest technology and computer forensics that will assist them in achieving the information needed. Private investigators will also be familiar with the Department of Revenue, State Treasury, Comptroller, State Controller, along with other financial administrators. They will also be accustomed to working with the Attorney General’s office and the State Tax Commission to get the information needed.
Private investigators will know where to look, where to begin, and what paperwork needs to be filled out if necessary. A private investigator is experienced in the process of unclaimed property. We have the tools and equipment required and will keep your information confidential and discreet.
Locating these funds or property can be time-consuming and costly if you don’t know where to start or look. It may also take resources that you don’t have or even have access to. Plus, a private investigator will also have connections in this area of expertise that help you get the information you need to claim the property or money you forgot about or inherited. They will do all the footwork so you can continue with life and not sacrifice any unnecessary time trying to do it yourself.
When it comes to asset recovery, it isn’t a judgment collection. While a part of it revolves around it, a good private investigator knows that if your case is based on enforcing a judgment, then those assets are more than likely long gone. Asset recovery involves specialized knowledge along with the simultaneous application of common and civil litigation tactics, investigative principles, forensic accounting techniques, insolvency options, forfeiture schemes, and a mindset steeped in strategy and know-how.
A successful private investigator will have an inquiring mind, cultural sensitivity, flexibility, resilience, adaptability, and a lot of patience. While you may see patience as a virtue in other areas of life, asset recovery can be a slow process. If you’re looking to hire a private investigator to help with your asset recovery investigations case, then acceptance of a possible slow timeline is a possibility. While your private investigator may work as fast as they can, there can be many legal procedures a private investigator may have watched play out before they can move forward.
SPYWARE: AN INTRODUCTION
Mobile devices hold intimate details of our lives and this single access point for information is usually convenient. But for survivors of domestic violence, sexual violence, or stalking, an abusive person can misuse spyware to access a terrifying amount of information.
This document includes information about how to identify a spyware case, how and where to look for evidence of spyware, and tips for gathering evidence.
SPYWARE: THE TECHNOLOGY
“Spyware” refers to software applications that give a person remote access to a device, allowing them to monitor and collect information and device activity. To install spyware on a mobile device, a person generally must have physical access to the device or convince the user to install the software, often through deception. For Apple products, devices will generally need to be jailbroken before these applications can be installed.
Dual-Use Applications and Tools That Can Be Misused
In addition to spyware applications that have the main purpose of remotely spying on someone, there are also applications that have legitimate purposes but can be misused to access a device remotely or receive data from it. Dual-use applications may be purposefully downloaded by the user and they may not even be aware the abusive person has remote access to their device data through it. For example, the Find My Friends or Find My iPhone applications on iPhones can be used to surreptitiously track a user.
There are also many applications with secondary features that share location data. For example, if certain settings are used, Snapchat or Google Maps may be misused to access the location information of someone’s device. Depending on what information the abusive person knows, it may be helpful to assess for the misuse of these types of apps as well. Though the use of spyware in domestic violence, sexual violence, and stalking cases has been well-documented for almost two-decades—first with computers and now with mobile devices—the methods used to monitor and collect information about survivors are often and may or may not include spyware. It can be useful to start an investigation by considering all possible sources –including non-spyware options—for how an abusive person could be inappropriately obtaining information.
Step 1 – Give the survivor the benefit of the doubt
help them document behaviors and events to see if there is a pattern. For example, the abusive person might show up at places the same time as the survivor or may drop hints that they are collecting information about the survivor. In one case, a survivor was looking at a particular pair of shoes online, and shortly after the abusive person sent the survivor the exact URL and said they would look great on her. Hints, however, are not always so blatant. It is important to walk through experiences that have caused the survivor concern.
Step 2 – Identify what information the abusive person is accessing.
Identify each piece of information that the abusive person appears to have access to. For instance, if the abusive person consistently shows up at the survivor’s work, despite varying shift times, there may be a leak in the survivor’s workplace (i.e. a coworker) or the online scheduling software, or maybe the schedule is emailed to an account that is being monitored. If the survivor has gone to three different grocery stores and the abusive person has shown up each time, the abusive person may be accessing their real-time location through GPS.
Step 3 – Consider social explanations
The most common, non-technological explanation for an abusive person having too much information about a survivor is a friend or relative leaking the information. Friends or relatives might not understand the entire situation, and may unwittingly provide information. Alternatively, someone may be spying on the survivor and purposefully reporting to the abusive person.
Ask the survivor if any friends or relatives were privy to the information in question. Then, from that list of people, ask if any of them are or could be in contact with the abusive person. If so, the survivor may need to tell them to stop sharing information, or the survivor may need to stop sharing information with them.
Step 4 – Consider everyday features and apps that contain the information
An abusive person may inappropriately access information by misusing everyday features and apps used by the survivor. For example, they may know or have guessed a password or be physically looking through phone activity while the survivor’s phone is unattended.
Ask the survivor where each piece of information may be stored. Is the work schedule in their email? Does the abusive person have access to the Find My iPhone feature? Knowing where the information is located will help narrow the focus in determining how the abusive person is getting the information.
Step 5 – Consider information the survivor shares publicly
Some survivors may unwittingly share private information through publicly accessible accounts, including social media. For example, they may have posted about their work shifts and not realized the privacy setting was set to public.
It is important to understand what the survivor chooses to share about themselves and how. An online search for the survivor can be helpful. Identify what social media platforms are used and then identify what information is accessible or visible to the general public. They may be posted publicly, rather than privately or the abusive person may be connected to a third party who can see that activity.
Help survivors review privacy settings so they can make informed choices about who has access to their information.
Step 6 – Look for evidence of spyware.
If no other leaks of information can be identified or if the abusive person knows too much without explanations, look for evidence of spyware.
Identify Types of Evidence
The existence of spyware can be difficult to uncover as the application may be hidden or may not clearly disrupt the regular use of the device. It can be especially difficult to prove the misuse of dual-use applications because it must be shown that the application is present and that it is being manipulated to obtain remote access to device data without the survivor’s knowledge or permission, or with coerced permission.
Protect all of the mobile device’s data.
In some cases, direct evidence of spyware on a mobile device can only be obtained with the help of a forensic professional. It is important to protect all data since you may not know immediately what to look for and it may be needed later by a forensic professional.
Throughout your investigation and evidence collection process, help the survivor build a picture of what leads them to believe spyware is being used. They may have seen a receipt for a spyware company on the abusive person’s computer or the survivor may have information that the abusive person used this type of software against another person. Even without this information, asking open ended questions may encourage a survivor to share information that may help the investigation.
NOTE ABOUT PASSWORDS: Usually when technology is used to facilitate abuse, it is a good idea to help the survivor to change their passwords and to disconnect other devices from accounts. However, if spyware is on the device, it is not safe to change passwords on that device. Create a plan on how to change passwords without alerting the abusive person, such as using a separate, safer device. Once a plan is created, you can help the survivor create strong passwords.
Create a list of information that will help the case.
You may not know all the experiences that have led the survivor to believe the abusive person has access to information, which limits your knowledge of what experiences are relevant. The survivor may not be familiar with the justice system and may be unaware of what is most important for court. Have a detailed conversation with the survivor, and encourage them to share as much detail about the situation as they can remember. It is also important to be very clear about what kind of information you are seeking.
NEXT STEPS IN YOUR INVESTIGATION
Spyware misuse is one of the most invasive forms of tech abuse, and investigations can be extremely complicated. However, it is possible to successfully prove spyware cases through effective investigation and creative advocacy. Contact V.I.G. to get started on your investigation today.
What is Data Extraction?
Data extraction is the process of collecting or retrieving disparate types of data from a variety of sources, many of which may be poorly organized or completely unstructured. Data extraction makes it possible to consolidate, process, and refine data so that it can be stored in a centralized location in order to be transformed. These locations may be on-site, cloud-based, or a hybrid of the two.
Data extraction is the first step in both ETL (extract, transform, load) and ELT (extract, load, transform) processes. ETL/ELT are themselves part of a complete data integration strategy.
Data Extraction and ETL
To put the importance of data extraction in context, it’s helpful to briefly consider the ETL process as a whole. In essence, ETL allows companies and organizations to 1) consolidate data from different sources into a centralized location and 2) assimilate different types of data into a common format. There are three steps in the ETL process:
Extraction: Data is taken from one or more sources or systems. The extraction locates and identifies relevant data, then prepares it for processing or transformation. Extraction allows many different kinds of data to be combined and ultimately mined for business intelligence.
Transformation: Once the data has been successfully extracted, it is ready to be refined. During the transformation phase, data is sorted, organized, and cleansed. For example, duplicate entries will be deleted, missing values removed or enriched, and audits will be performed to produce data that is reliable, consistent, and usable.
Loading: The transformed, high quality data is then delivered to a single, unified target location for storage and analysis.
The ETL process is used by companies and organizations in virtually every industry for many purposes. For example, GE Healthcare needed to pull many types of data from a range of local and cloud-native sources in order to streamline processes and support compliance efforts. Data extraction was made it possible to consolidate and integrate data related to patient care, healthcare providers, and insurance claims.
Similarly, retailers such as Office Depot may able to collect customer information through mobile apps, websites, and in-store transactions. But without a way to migrate and merge all of that data, it’s potential may be limited. Here again, data extraction is the key.
Data Extraction without ETL
Can data extraction take place outside of ETL? The short answer is yes. However, it’s important to keep in mind the limitations of data extraction outside of a more complete data integration process. Raw data which is extracted but not transformed or loaded properly will likely be difficult to organize or analyze, and may be incompatible with newer programs and applications. As a result, the data may be useful for archival purposes, but little else. If you’re planning to move data from a legacy databases into a newer or cloud-native system, you’ll be better off extracting your data with a complete data integration tool.
Another consequence of extracting data as a stand alone process will be sacrificing efficiency, especially if you’re planning to execute the extraction manually. Hand-coding can be a painstaking process that is prone to errors and difficult to replicate across multiple extractions. In other words, the code itself may have to be rebuilt from scratch each time an extraction takes place.
Benefits of Using an Extraction Tool. Digital Forensics Companies and organizations in virtually every industry and sector will need to extract data at some point. For some, the need will arise when it’s time to upgrade legacy databases or transition to cloud-native storage. For others, the motive may be the desire to consolidate databases after a merger or acquisition. It’s also common for companies to want to streamline internal processes by merging data sources from different divisions or departments.
If the prospect of extracting data sounds like a daunting task, it doesn’t have to be. In fact, most companies and organizations now take advantage of data extraction tools to manage the extraction process from end-to-end. Using an ETL tool automates and simplifies the extraction process so that resources can be deployed toward other priorities. The benefits of using a data extraction tool include:
More control. Data extraction allows companies to migrate data from outside sources into their own databases. As a result, you can avoid having your data siloed by outdated applications or software licenses. It’s your data, and extraction let’s you do what you want with it.
Increased agility. As companies grow, they often find themselves working with different types of data in separate systems. Data extraction allows you to consolidate that information into a centralized system in order to unify multiple data sets.
Simplified sharing. For organizations who want to share some, but not all, of their data with external partners, data extraction can be an easy way to provide helpful but limited data access. Extraction also allows you to share data in a common, usable format.
Accuracy and precision. Manual processes and hand-coding increase opportunities for errors, and the requirements of entering, editing, and re-enter large volumes of data take their toll on data integrity. Data extraction automates processes to reduce errors and avoid time spent on resolving them.
Types of Data Extraction
Data extraction is a powerful and adaptable process that can help you gather many types of information relevant to your business. The first step in putting data extraction to work for you is to identify the kinds of data you’ll need. Types of data that are commonly extracted include:
Customer Data: This is the kind of data that helps businesses and organizations understand their customers and donors. It can include names, phone numbers, email addresses, unique identifying numbers, purchase histories, social media activity, and web searches, to name a few.
Financial Data: These types of metrics include sales numbers, purchasing costs, operating margins, and even your competitor’s prices. This type of data helps companies track performance, improve efficiencies, and plan strategically.
Use, Task, or Process Performance Data: This broad category of data includes information related to specific tasks or operations. For example, a retail company may seek information on its shipping logistics, or a hospital may want to monitor post-surgical outcomes or patient feedback.
Once you’ve decided on the type of information you want to access and analyze, the next steps are
1) figuring out where you can get it and
2) deciding where you want to store it. In most cases, that means moving data from one application, program, or server into another.
A typical migration might involve data from services such as SAP, Workday, Amazon Web Services, MySQL, SQL Server, JSON, SalesForce, Azure, or Google Cloud. These are some examples of widely used applications, but data from virtually any program, application, or server can be migrated.
Data Extraction in Motion
Ready to see how data extraction can solve real-world problems? Here’s how two organizations were able to streamline and organize their data to maximize its value.
Advancing Education with Data Integration
Over 17,000 students attend Newcastle University in the UK each year. That means the school generates 60 data flows across its various departments, divisions, and projects. In order to bring all that data into a single stream, Newcastle maintains an open-source architecture and a comprehensive data management platform to extract and process data from each source of origin. The result is a cost-effective and scalable solution that allows the university to direct more of its resources toward students, and spend less time and money monitoring its data integration process.
The Cloud, IoT, and The Future of Data Extraction
The emergence of cloud storage and cloud computing has had a major impact on the way companies and organizations manage their data. In addition to changes in data security, storage, and processing, the cloud has made the ETL process more efficient and adaptable than ever before. Companies are now able to access data from around the globe and process it in real-time, without having to maintain their own servers or data infrastructure. Through the use of hybrid and cloud-native data options, more companies are beginning to move data away from legacy on-site systems.
The Internet of Things (IoT) is also transforming the data landscape. In addition to cell phones, tablets, and computers, data is now being generated by wearables such as FitBit, automobiles, household appliances, and even medical devices. The result is an ever-increasing amount of data that can be used drive a company’s competitive edge, once the data has been extracted and transformed.
Data Extraction on Your Terms
You’ve made the effort to collect and store vast amounts of data, but if the data isn’t in a readily accessible format or location, you’re missing out on critical insights and business opportunities. And with more and more sources of data appearing every day, the problem won’t be solved without the right strategy and the right tools.
Talend Data Management Platform provides a comprehensive set of data tools including ETL, data integration, data quality, end-to-end monitoring, and security. Adaptable and efficient, Data Management takes the guesswork out of the entire integration process so you can extract your data when you need it to produce business insights when you want them. Deploy anywhere: on-site, hybrid, or cloud-native.
Pre-litigation refers to the legal process that happens before a lawsuit is filed. The investigation phase is extremely important as it builds the foundation for a successful case. Facts, documents, medical records, employment records, police reports, and witness statements are all gathered and thoroughly examined.
Litigation investigations are used in various areas of the law, especially where cases become quite complicated and require previously uncovered evidence, witnesses, and more. Here are just some of the areas of the law that benefit from litigation investigations:
- Civil litigation: Normal discovery, especially in complex civil litigation cases, may not produce the quality evidence needed for your case. Limiting yourself to subpoenas and discovery requests can affect the effectiveness of your arguments, thereby impacting your ability to achieve the best possible outcome for your client. Private litigation investigations can locate new witnesses, interview potentially involved parties, conduct computer forensics searches, perform background checks, conduct surveillance, determine the relationship of parties, and much more.
- Labor and employment litigation: Whether you are prosecuting or defending an employer or employee, an experienced investigative team is a major asset in cases involving misconduct or internal threats. We routinely conduct investigations into FMLA abuse, EEOC complaints, theft and fraud, misuses of company assets, violations of non-compete and non-disclosure agreements, and theft of trade secrets.
- Intellectual property investigations: When you are managing the research of a nuanced intellectual property case, you want a professional investigative team that can deliver accurate information and is flexible about your chosen approach to your case. Proper collection and delivery of evidence is essential. Intellectual property investigations often focus on patents, product diversion and parallel importation, channel checking, and trademarks.
- Criminal defense investigations: Validating the work performed by law enforcement, and even augmenting or correcting it, is an invaluable skill that experienced private investigators can contribute to a criminal defense case. Gathering sources, witnesses, and evidence previously uncovered aids attorneys as they complete discovery for a case.
Whatever area of law you practice, and often frustrating and time-consuming element of the case you’re working on is locating witnesses and defendants. Advanced investigative tools are a critical element in finding where a difficult-to-locate subject physically resides or works – whether locally, domestically, or abroad – rather than just acquiring a mailing address attached to their name. Private investigators have the capability to find the people and information you’re seeking.
Techniques Used to Conduct a Litigation Investigation
Comprehensive services, resources, and techniques allow an experienced private investigative team to work closely with law firms, attorneys, and corporate legal departments to conduct thorough litigation investigations. We obtain sensitive information discreetly using methods such as:
- Asset investigation and analysis
- Computer usage verification
- Corporate threat assessment
- Surveillance
- Due diligence investigations
- Witness location
- Computer forensics
- Detailed background checks
- Affair surveillance
- Interviews
- Statement taking
Expert private investigative teams that specialize in litigation investigations provide invaluable attorney support services to supplement in-house legal research. Technological advances make legal cases that much more complicated today, and this fact requires that much more expertise and assistance in finding and deciphering computer forensics.
Why Hire ASG to Conduct Your Litigation Investigation?
Under the direction of legal counsel, our legal service support investigations group provides thorough and extensive litigation investigations. We understand the investigative needs of attorneys, what qualifies as proper evidence, and how to conduct investigations that provide admissible evidence in cases.
Our investigative experience, training, networks, and research tools are extensive, and we are supported by a network of specialists, both domestically and abroad. ASG has exceptional reach and capabilities where your litigation investigation is concerned. All communications and information gathered remain completely confidential.
ASG is a full-service investigative agency with a strong arm in litigation investigation. It is our goal to provide high-quality litigation support, whatever your case needs may be. Call us today to discuss your cases. Find out how the experts at ASG can add value to your efforts.
V.I.G Services
What's Included
Each case includes a discovery phone call to understand the case & services you are hiring us for.
How it Works
Once you have decided we are the correct investigator for you, we will send you a contract for you to review, sign, and pay a retainer.
Services & Pricing
During your discovery call, an investigator will help create a custom plan detailed to fit your needs and gather vital information to start.

Secure Client Communication
We understand your case is extremely sensitive and confidential, which is why we make sure that your data is safe and secure.
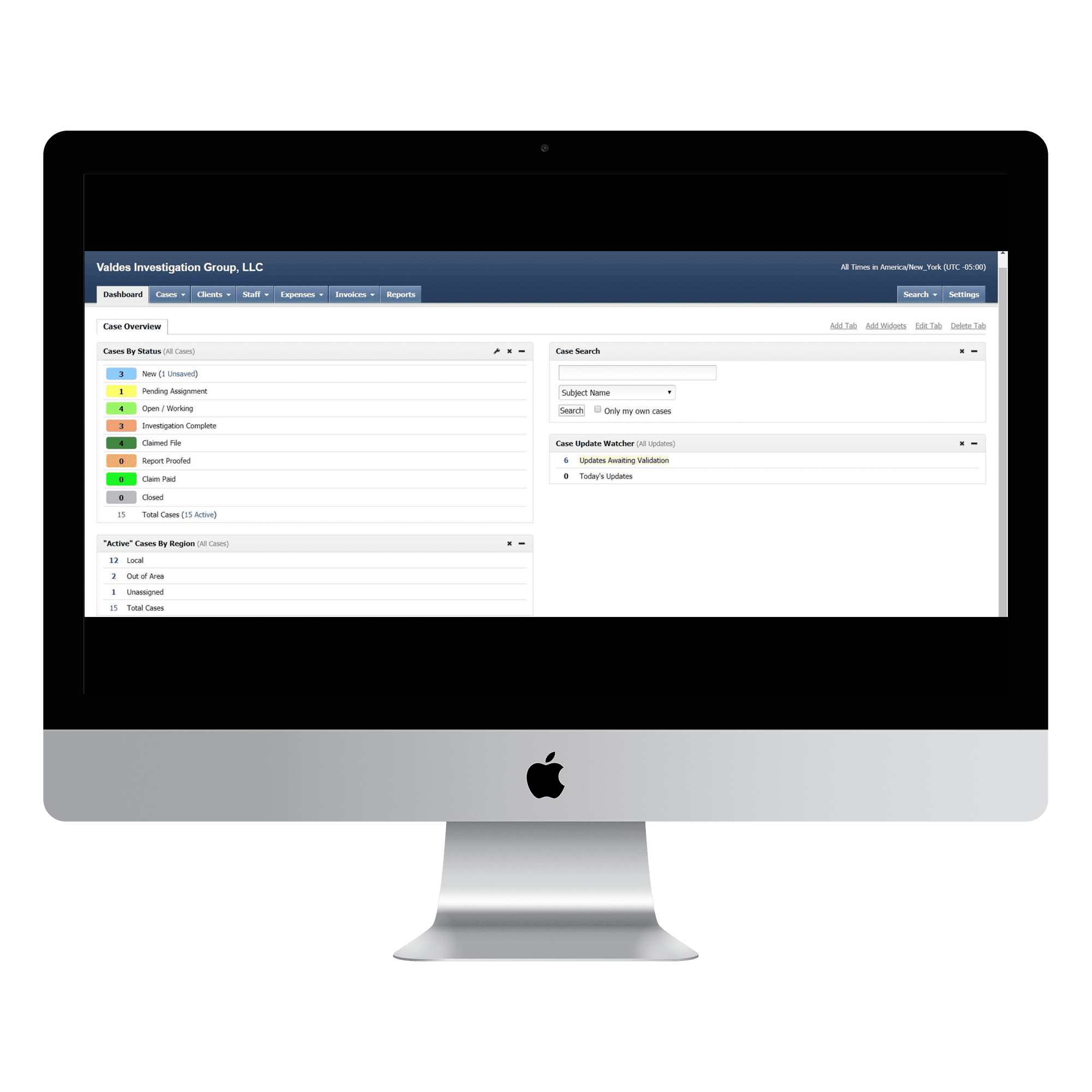
- Important Case Details
- Client communication
- Videos, Photos, Etc.
- All Case Documents
- Easy to manage dashboard
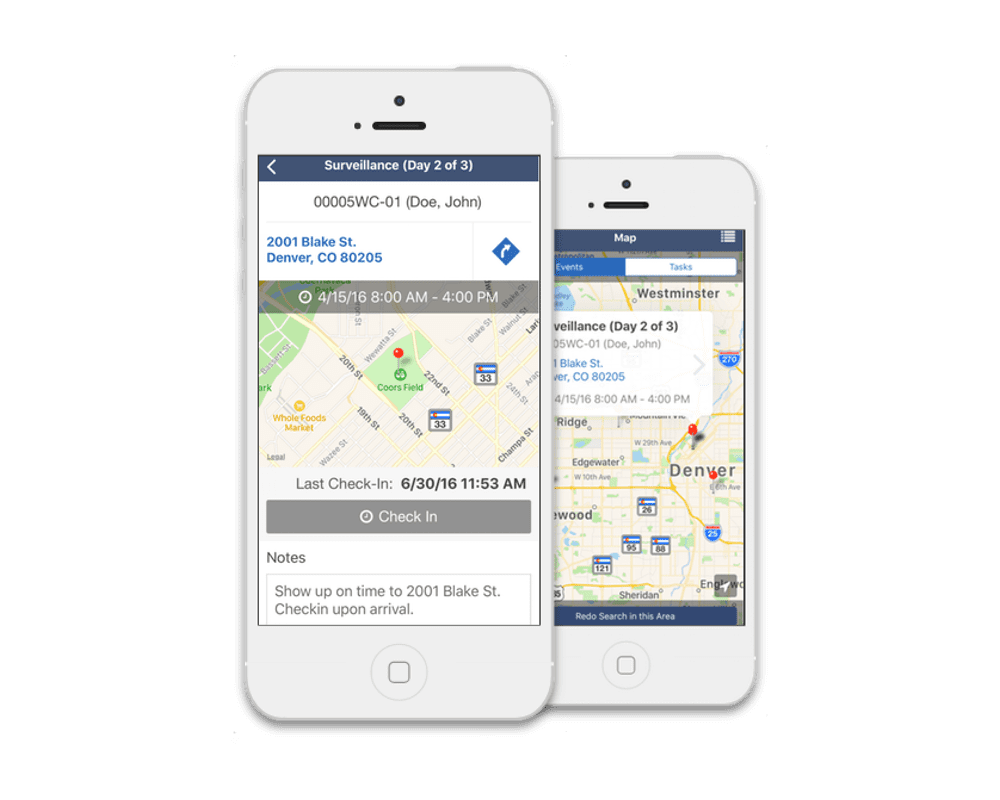
- Access to case data
- Geolocation based activity
- Mobile time & distance tracking of P.I.’s
- Time and expense tracking
Frequently Asked questions
Cant SEE DONT TOUCH
Private Investigator Near Me
What Services Do Private Investigators Offer?
Private investigator services vary widely based on a client’s needs. Some private investigators specialize in a single area, or a few areas, while others provide a full breadth of services. Most private investigation agencies hire private investigators with diverse backgrounds in order to provide a wider range of services to their clients.
When hiring a PI, be sure to inquire about the types of services they provide and ask to see examples of supporting case materials or references to contact.
List of Private Investigator Services
Following is a list of different types of investigations:
- Accident Investigation
- Arson / Fire Investigation
- Background Investigation
- Child custody
- Civil Investigation
- Corporate / Business
- Crime scene investigations
- Criminal
- Fraud Investigation
- Insurance / Insurance Fraud
- Missing Person
Following is a list of the different types of services that a private investigator may provide:
- Adoption Inquiries, research and locates
- Address History and Address Verification
- Adult / Child Abduction (see Missing Persons)
- Asset search and recovery
- Automobile Recovery and repossession
- Bail enforcement (see Bounty Hunter)
- Bankruptcy verification
- Bug sweeping to identify surveillance technology
- Business Credit Checks
- Civil Litigation Support
- Civil Court Records research and retrieval
- Court records search and retrieval
- Credit History Check
- Criminal defense investigation
- Criminal investigation
- Debtor Locates
- Delivery of Subpoenas, also known as process service
- Digital Video Surveillance
- DNA Lab Testing Services – For determining paternity, infidelity, testing ancestry, kinship, blood/alcohol, personal identification
- DUI or License Suspensions
- Cheating Spouse surveillance
- Collection of Debts
- Computer Forensics and data analysis
- Court Records Search
- Covert Surveillance Operations
- Divorce investigations
- Death Investigation
- Document retrieval
- DMV / Motor Vehicle records search and retrieval
- Employment History
- Executive Protection
- Expert Witness
- Federal records search
- Fugitive recovery (see Bounty Hunter)
- Federal Criminal Record Search
- Fictitious Name Filings
- Fingerprinting
- Forensic Investigation
- GPS tracking
- Hidden camera surveillance
- Home security
- Homicide investigations
- Identity Theft
- Infidelity Investigations
- Internal theft investigations/loss prevention
- Invasion of Privacy
- Investigate police abuse
- Legal Experts
- Legal Testimony
- Locate missing persons
- Loss Prevention
- Malpractice investigation
- Marriage records
- Missing Person Locates
- Motor Vehicle Report Retrieval
- MVR (Motor Vehicle) Reports
- Mystery Shopper / Secret Shopper
- Night Time Surveillance
- Official Statements / Interviews
- Parental kidnapping
- Patent and trademark infringement
- Personal Injury
- Personal Protection
- Phone Records
- Police Reports
- Polygraph
- Public document retrieval
- Public records search
- Pre-Employee Screening
- Pre-Marital Inquiries
- Property Records Retrieval
- Process Service
- Records Retrieval
- Recovery of Stolen Property
- Research prison records
- Sex Offender Registration
- Sex offender search – locate or investigate
- Sexual Harassment
- Service of Process
- Skip Trace
- Subpoena Service / Process Service
- Subrogation
- Stalking / Anti-Stalking
- State records search
- Surveillance
- Tenant Screening
- Testify in Court
- Trade Secret Violations
- Theft
- UCC Filings
- Unclaimed Property Research
- Undercover
- Vehicle Tracking Systems
- Vendor assessment
- Vessel / Aircraft
- Video Surveillance
- Wiretap detection
- Witness Location and Evidence Preparation
- Witness Interviews and Statements
- Workers Compensation Claims
- Wrongful or Suspicious Death
How much does it cost to hire an investigator ?
Hiring a private investigator can help in all kinds of situations ranging from finding a birth parent to improving personal security. Nationally, the average price range for private investigation is $95-$410, although pricing often hovers around $150 per hour depending on the complexity of the services you need.
What should I look for when hiring a private investigators services?
Many private investigators are hired by companies who need to look into threats, HR background checks, and potential business partners.
- Request a Discovery Call Meeting
Never hire a private investigator without meeting him or her in person. An in-person meeting will help you decide if this PI is the professional you can trust to be discreet and competent. Unfortunately, many private investigators run a solo practice based on their experience as an ex-cop or other skill. However, when you have a highly sensitive investigation, you need the support and professionalism provided at a higher level.
- Meeting in person will help you make a better first impression assessment of the investigator’s professionalism and manner. You might need your private detective to testify in criminal or civil court. You want to make sure your PI is a reputable representative of your case. If the PI cuts you off, doesn’t answer your questions or is vague, it’s probably not a good match. Remember, you are the client, and the private detective should be trying to win you as a client. You need to find a person that you trust. After all, you will have to share sensitive information with him or her. Trust your gut feeling on this one. If something about the private investigator seems off, thank them for their time and keep looking for a better fit.
- Ask to See Their Private Investigator License
Before you hire a private investigator, you must do your due diligence and ensure you choose a reliable and professional PI. First, ask to see his or her PI license. Check their license is valid in your state. Check for Insurance. One of the private investigator requirements is having insurance. Make sure you ask your PI before you hire him or her to show you proof of insurance. This protects you from being liable if anything happens to the private investigator during the investigation.
- Ask About Qualifications and Experience. You want to make sure that the private detective you hire is qualified to do the job and do it well. If the person has a website, review it to see if it lists his or her qualifications. Many private investigators are former police officers. But that’s not a good enough reason to hire someone. Years of police work won’t help you if you have a legal issue. In those cases, you need a civil and criminal case investigator. Make sure to ask your PI how many years of experience he or she has. You want to make sure your PI is qualified to investigate and possibly testify in the type of case you are hiring for. Ask how many cases similar to yours he or she has worked on in the past year. It’s best to choose a PI that specializes in the type of investigations you need. Not every private investigator excels at every type of case. So choose one whose strengths are the type of investigation you need. You also want to know if your case will be handled by just one PI or if there will be other private investigators on the case. They Should Engage With Professional Organizations. A private investigator might not necessarily be part of any professional organization. But if they are passionate and reputable, it is more likely. This is a good way to weed out fly-by-the-night companies who may scam you. Shady investigators won’t care about the newest legislature and continuing education. Some professional organizations that a private investigator might belong to include the National Association of Legal Investigators, the National Association of Investigative Specialists, and the National Council of Investigation and Security Services. Membership in these types of organizations will help you to see a company’s standing in the investigation community.
- Get Testimonials & References
Before you hire a private investigator, you’ll need to do a little investigation of your own.
- Go online and look up the company or private detective. It is important to run a query on the investigator as well as on the agency. Of course, investigative work is discreet. So if you don’t see much, that’s not necessarily a bad sign. Ask your PI to give you a list of three previous clients that you can contact as references. Be sure to ask about the private investigator’s professionalism, work ethic, and results.
- Ask to See a Work Sample
The end product, whether it’s a written report, a photo, or a video, is the evidence that you may need in court. This evidence must be of good quality. In many court cases, concrete proof can give you enough leverage to get a settlement without needing to go to court. A good investigator will likely show you examples of their work. If not, make sure to ask so you can get a good idea of what you can expect. For example, you’ll want photographs with time and date stamps marked. The report should be typed up and legible without any missing information. You’ll be able to learn a lot about the private investigator based on how thorough and detailed his or her reports are. - Avoid Cheap Pricing
When hiring a private investigator, don’t just shop around for the lowest price. Premium rates usually mean that the agency has a solid reputation that warrants the price. Budget private investigators either are struggling to get business or know that they can’t get excellent results. You don’t want to risk getting sub-standard service when your business is involved. Hire a professional investigator that has the experience and skillset to get results.
- Important Investigations Require Quality Investigators
There you have it! An in-depth guide for how to hire a private investigator for your business. Remember, in this field, experience, and professionalism span a considerable range. At OPS Security Group, we offer the very best discreet, experienced private investigation services.
Other Personal Investigator Services
Find A Person
We have advanced tools to help find any person located in the United States
Background Checks
Our expert background checks can include a wide range of information
Data Retrieval
Get important information extracted from any device in most conditions.
Process Serving
Experienced and efficient fixed price process servers in all states.
Due Diligence
We take reasonable steps to ensure you avoid committing any offense
Dating Site Scams
Take steps to protect yourself against romance scams or being catfished
Locating Assets
We can help you discover and retrieve unclaimed assets that are rightfully yours
Bug Sweeps - TSCM
We can sweep the affected area for any bugs or always listening devices
Electronic Takeouts
Retrieve a copy of your data from Google, Apple, Facebook, and more platforms
Insurance Claim Investigations
Prevent paying out for fraudulent or unwarranted insurance claims
Remote Digital Forensics Services
We have the ability and credentials for any digital forensics service.
Relationship Investigations
Verify your partners loyalty with our relationship investigation service.
Our Pricing Plans
Being one of the nation’s oldest private investigation groups, we have created customized affordable packages for all our investigation services offered. Please fill our our form below then book a meeting for a free discovery call.








